Best free VPN apps
We roundup the best free VPN services for 2018 to help you browse anonymously

Virtual Private Networks (VPNs) let you use the internet anonymously, concealing your identity as if you're connecting via an alternative service or from somewhere different to where you really are.
It all sounds a bit sneaky, like something out of a high-tech espionage novel or a hacking tool to evade detection from the government or activists, but using a VPN is useful for anyone worried about their browsing security. It's particularly useful for at-risk groups such as human-rights campaigners or anyone using a public Wi-Fi for working remotely. It also plays a rather important role in the business world and can be used to build a layer of security.
Simply, when using a VPN, it means your location is concealed, leaving you to act as if you are not attached to your current location, which is a great option for testing out services that are usually only available if you're in a certain place.
Some VPN services can be quite expensive, particularly if it's not something you need to use all the time, but there are enough free VPN services that provide a decent level of quality without the financial burden.
Keep reading for our guide to the best free VPN's.
Browsec
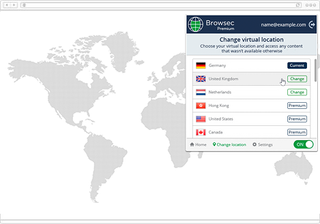
Browsec is a browser plugin that is supported for Chrome, Firefox, Opera and on iOS and Android if you want to stay anonymous on any device you may own. It features a clear and easy to use UI and you won't need to input any of your details to use it.
It's fast, totally free and there aren't even any annoying ads to deal with. An upgrade option exists if you want to speed up your connection, but this isn't needed for most tasks you may want to undertake without giving your identity or location away.
Cyberghost
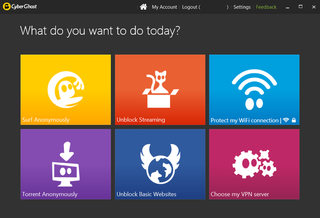
Like most VPN tools, Cyberghost is available for free, but also has premium, paid-for tiers available too, for those that want to boost their connection. The free version shouldn't be sniffed at though, because it offers full, unlimited VPN access and although isn't completely reliable for intensive applications like streaming video, it's good enough for general browsing.
It's available as a desktop client, which uses OpenVPN to connect to the internet and with servers dotted around the world, you can choose pretty freely from which country you would like to connect via.
Freelan
Freelan is one of the more complicated free VPN services in our roundup, because it's open source and requires some command line work to get connected. It installs software on network drivers on your computer to re-reroute web traffic, but that all has to be done via the command line rather than a graphical interface.
However, if you're comfortable tweaking with your machine on a much deeper level rather than just using a browser plugin or desktop app, Freelan offers a whole lot more than its simpler rivals.
TunnelBear
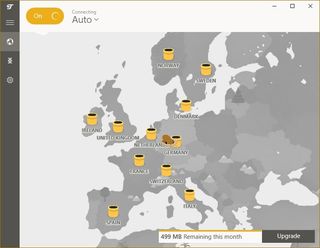
TunnelBear's Little plan is its free offering, which offers up to 500GB of free browsing data every month. After that, you'll have to upgrade to Giant Bear for $7.99 for unlimited data if you want to subscribe to a monthly plan or $49.99 for the whole year. The free plan itself is pretty good if you don't need to use a VPN very often and with 20 servers located around the world, it's pretty likely you'll be able to find one in your specified region.
Probably the most impressive feature of TunnelBear is that you can connect up to five devices at the same time, including desktop, mobile, tablet and router. GhostBear is the service's extra-secure addition on Mac OS X, Android and Windows that claims to make your data undetectable even to governments, ISPs and businesses.
WindScribe

WindScribe also offers a free version with a download limit, although here, you can use up to 10GB of data without splashing out (provided you sign up with your email address, 2GB without registering), making it a better option for those that need to stream content. It also benefits from unlimited device connections across Windows, Mac, iOS and Android.
However, it's not as fast as some of the other freebies, so it's likely you'll want to upgrade to a faster, paid-for service. Also, WindScribe only has servers in eight locations, so you may be limited by that too.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
Bobby Hellard is ITPro's Reviews Editor and has worked on CloudPro and ChannelPro since 2018. In his time at ITPro, Bobby has covered stories for all the major technology companies, such as Apple, Microsoft, Amazon and Facebook, and regularly attends industry-leading events such as AWS Re:Invent and Google Cloud Next.
Bobby mainly covers hardware reviews, but you will also recognize him as the face of many of our video reviews of laptops and smartphones.





