IT Pro Verdict
Pros
- +
Clever call handling features
- +
Outstanding value
- +
Fast deployment
- +
Excellent site management options
Cons
- -
Video conferencing not supported on iOS
SMBs that want a cloud telephony system they can rely on will find the Voip Exchange (VE) service from UK-based Voip Unlimited offers many compelling features. Unlike providers that use third-party cloud platforms, it’s hosted on Voip Unlimited’s own dedicated network in three UK data centres for resiliency and it’s optimised for voice traffic, making it ideal for home workers with limited broadband speeds.
Costs are easily managed, with the base licence starting at £8.50 a month per seat with a minimum one-year contract. This package requires each user to have a desk phone, which VoIP Unlimited can supply, but if you already have compatible phones, it will re-provision them for its service.
Two separate packages are aimed at users that don’t need a desk phone: one provides iOS and Android mobile apps and the second adds a Windows desktop app. The mobile suite package looks good value as it costs £17.50 a month for each seat, enables all apps plus every VE feature and includes 3,000 minutes for outbound calls to landlines and mobiles.
As you’d expect from a hosted VoIP service, VE is easy to deploy. Our account was set up to our requirements by a technician, who assigned numbers for our specific area code plus a group of users as we requested. We asked for Yealink desk phones to be supplied and, as these were pre-registered to our account, we simply connected them to our PoE switch to provision them.
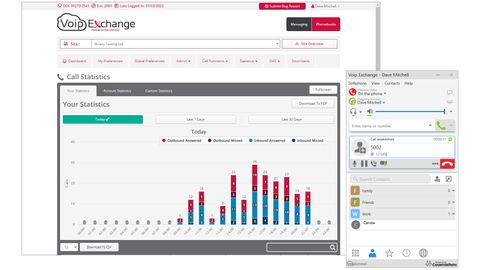
The VE web portal is well designed and easy to navigate. A wizard helps create new users where we provided their personal details, added them to departments, chose a desk phone for them and assigned it a direct dial in (DDI) number.
A feature that will appeal to businesses with distributed offices and home workers in different locations is the option to add extra sites under the top-level business account. These allow different settings to be applied to groups of users and centrally managed from one portal.
Each user receives a personal portal so they can record greeting messages and upload them as WAV files. If permitted, they can set up call twinning so another device such as a mobile rings for incoming calls and use call forwarding when out of the office to redirect inbound calls to another number.
Video conferencing meetings are supported too. Users join by dialling a conference room number, providing a PIN and selecting the camera option on their app. We found that iOS is currently unsupported, but it works fine on Windows, macOS and Android devices.
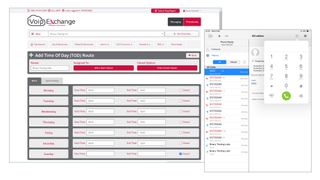
The interactive voice response (IVR) service adds a professional touch, as you can create a digital receptionist to present callers with a menu of up to 12 options. Record a custom greeting message and you can add multiple branch operations to direct callers to a specific extension, an external number, hunt groups or voicemail, and use time-of-day periods to determine when the IVR is active.
Hunt groups ensure calls are never missed, as you define groups of users so incoming calls to the assigned DDI will ring all phones at once or call each one in strict order. If the call isn’t answered within a period of up to two minutes, you can forward the call to a specific user, an external number, another hunt group or to the IVR.
Ease of use and a swift deployment makes Voip Exchange a great choice for SMBs and home workers. Call-handling features are outstanding, it’s simple to manage and the flexible call plans make it very affordable.
Dave is an IT consultant and freelance journalist specialising in hands-on reviews of computer networking products covering all market sectors from small businesses to enterprises. Founder of Binary Testing Ltd – the UK’s premier independent network testing laboratory - Dave has over 45 years of experience in the IT industry.
Dave has produced many thousands of in-depth business networking product reviews from his lab which have been reproduced globally. Writing for ITPro and its sister title, PC Pro, he covers all areas of business IT infrastructure, including servers, storage, network security, data protection, cloud, infrastructure and services.