Best Windows 10 tips and tricks for power users
A roundup of some of the most sophisticated Windows tweaks designed for power users in mind
Forget easy Windows tips - these ones are for those looking to get the most out of Microsoft's latest operating system, whether that's identifying battery thieves, syncing SMS messages to your desktop, or setting up a Linux VM.
Below we've rounded up ten sophisticated ways to take full advantage of the power on offer in Windows 10, including many that were new to us until we started digging, and a handful that are new to the world as part of recent updates.
1. Customise the power user menu
You're a power user, so you know about the Power User menu in Windows 10, right? The one that appears when you right-click on the Start button or press Windows+X. Good, just checking.
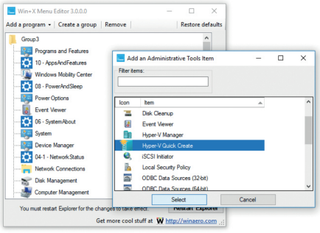
What you might not know is that you can customise this menu, removing features that you'll never bother with (I can't recall ever needing the Event Viewer, for instance) or replacing them with ones that you'll need more often (such as the Hyper-V Quick Create tool we cover later in this feature).
To customise the Power User menu you will need to download a small applet called Win+X Menu Editor from here.
Once installed, you can edit each of the three different groups in the Power User menu (extra points if you'd already spotted it was divided into three), or create a new group of your own. You can add functions from the Control Panel or Administrative Tools, or you can add specific applications if you wish, although that rather defeats the object of the main Start menu.
If you bodge it up, you can always restore the default menu.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
2. Identify the battery thieves
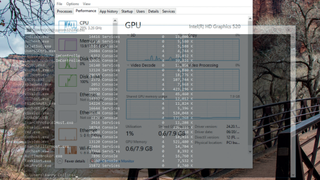
Common sense is normally a fairly good guide to which apps are burning through your laptop's battery. Adobe Premiere rendering a 4K video is going to be smashing through more battery than Word, I think we can all agree.
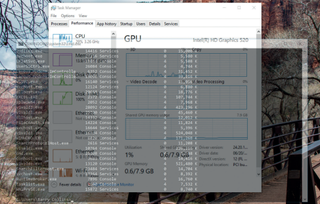
However, you don't have to rely on educated guesswork anymore. The latest Windows update has enhanced the information available in the Task Manager, with two new columns showing "Power usage" and "Power usage trend". The former is the amount of power the app is draining at present, while the latter reveals its impact over time.
If you suddenly notice your battery indicator plummeting like Theresa May's approval ratings, fire up the Task Manager and see if there are any glowing red apps in the Power usage column.
Whilst we're poking around the revamped Task Manager, you might notice another new column in there called GPU engine. This reveals if an app is leaning on the GPU's 3D engine and you can often find some surprising results. We wouldn't have assumed a Word doc without graphics would be troubling the 3D engine, but then we would have been wrong.
3. Set up a Windows kiosk
This is a tip that most IT admins or consultants will find particularly useful. In a business, sometimes there is a need to use a Windows device for a certain purpose. For example, maybe you have to set up an internet kiosk for the company's reception or even a laptop to run Spotify so that a venue or shop can play music.
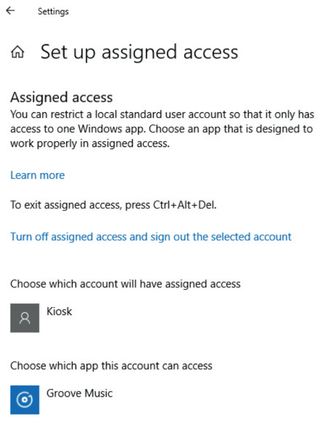
It is paramount that the users of that device cannot access anything other than the single app you have designated it for, as it's not necessary. For these specific use cases, it is always useful to effectively create a kiosk user account that can only access one Windows Store application.
To begin, first set up a secondary user account on the computer (this cannot be done on the main admin account for, hopefully, obvious reasons). Pay no attention to Microsoft's attempts to create a Microsoft account for the new user you just created and click on the option that says "I don't have this person's sign-in information" and "Add a user without a Microsoft account" in the user setup wizard that appears. It's up to you, but it may not be necessary to have a password on this account as it will only have access to a single app.
Once you have set up this new user account, return to the admin account and type "assigned access" into the Windows 10 search bar and choose the option that says "Choose an account for assigned access".
Select the account you have recently created and then choose the application you want the account to be able to access. Be aware that the app you want to use must already be provisioned for the account you're using. This means that if you want to provision an app that's not one of the core Windows apps, download it from the Windows Store in the new user's account.
As of October's Windows 10 update, you can also assign the Edge browser as a kiosk app. One example case is to provide an internet kiosk in reception, for getting guests to sign in via a page on the company's intranet.
Microsoft has a special page dedicated to deploying Edge in a kiosk scenario, which is worth reading.
Note that, when you want to exit the kiosk account, you must use Ctrl+Alt+Del because the account doesn't have access to the Start menu and its various power/login options.
4. Deal with SMS messages from your desktop
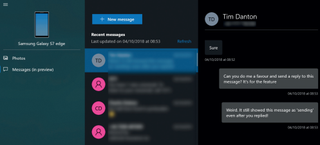
Being an iPhone user comes with the advantage of having been able to read and respond to SMS messages on their Macs for many years. Thankfully, Windows has taken steps in the right direction by introducing the Your Phone app in the October update.
For now, this feature only functions with Android handsets, but iPhone support is coming if Apple is willing to loosen the padlock on its SMS services.
With Your Phone, you're able to read and send SMS messages from the desktop app. Incoming messages also display a Windows notification, which is handy if you've got the phone on silent during a meeting, for example.
The service is most immediately useful for authentication codes. Some banks send out SMS codes to authorise payments, for example, meaning you don't have to dip into your pocket to copy the code into your web browser.
At the time of writing, the Messages facility was still "in preview" and there are certainly a couple of bugs that need to be squashed. When we sent a test message to the editor of this fine organ, the message appeared to get stuck with a spinning progress wheel which continued to display even after he had replied! When the wheel eventually stopped, the messages were displayed out of chronological order, as you can see from the screenshot above.
Also, something to watch for next year, the Your Phone app will begin mirroring Android apps on your desktop. We've already seen apps such as BlueStacks offering Android emulation on the desktop, but this could and we do stress could allow you to run your favourite mobile apps on the desktop without having to create fresh installations.
5. Make a command prompt transparent
Are you rattling commands into a Command Prompt but want to keep an eye on what's happening beneath the Command Prompt window? You can now make the Command Prompt window transparent, letting you see what's going on in the background. There are two ways to pull this off. With the Command Prompt window selected, you can hold down the Ctrl and Shift keys, and then use the mouse scroll wheel to adjust the level of transparency.
Alternatively, you could hold down the Ctrl and Shift keys and use the + and keys to achieve the same effect.
Adam Shepherd has been a technology journalist since 2015, covering everything from cloud storage and security, to smartphones and servers. Over the course of his career, he’s seen the spread of 5G, the growing ubiquity of wireless devices, and the start of the connected revolution. He’s also been to more trade shows and technology conferences than he cares to count.
Adam is an avid follower of the latest hardware innovations, and he is never happier than when tinkering with complex network configurations, or exploring a new Linux distro. He was also previously a co-host on the ITPro Podcast, where he was often found ranting about his love of strange gadgets, his disdain for Windows Mobile, and everything in between.
You can find Adam tweeting about enterprise technology (or more often bad jokes) @AdamShepherUK.





