10 best features of Microsoft 365 for small businesses
Microsoft 365, formerly Office 365 for small businesses, provides a comprehensive platform with all the tools a team could need
Formerly Office 365, Microsoft 365 is a comprehensive tool with multiple applications to aid your business. Office 365 for small businesses has been, and continues as Microsoft 365 to be, a complete service that makes it easy to collaborate on projects, store data, configure your IT infrastructure, and more, and provides one of the best email providers in Microsoft Outlook.
In this article, we'll run through the top 10 features that make this group of products ideal for small business owners. Read on to find out whether Microsoft 365 could help make your business more productive - and when you've finished, make sure to read our guide to the best Microsoft Office alternatives too.
1. Secure data storage

Microsoft's OneDrive is included in your Microsoft 365 package, and it enables you to store up to 1TB of data safely and securely. Microsoft has invested heavily in making OneDrive as secure as it can be, and goes to great lengths to maintain it, including a zero-standing access policy that ensures engineers cannot access user accounts unless they are specifically requested to.
OneDrive is also a brilliant vessel for collaboration. It enables you to share and collaborate on Microsoft apps in real time from any location and on any compatible device, safe in the knowledge that your files are securely backed up at all times. Read our OneDrive review to see what we thought of the service.
2. Company-wide licensing
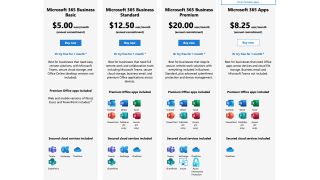
Licensing can be a major headache for small business owners. Multiple software licenses can be expensive and difficult to navigate. You may find yourself in a situation where only a few members of your staff require certain types of software, so it can be hard to justify the expense.
With Microsoft 365, your single license fee covers all of the software solutions provided by the platform. This one-off payment is much easier to manage, and enables predictable pricing so you can budget better. Even if you have staff members that don’t use certain products, it doesn't matter since those products are included as standard.
3. Market-leading word processor
It’s highly likely that most, if not all, of your staff will require the use of a word processing platform at some point. Microsoft Word is by far the best known and most widely used word processing software available. Your staff are likely well aware of the software and therefore already competent in using it.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
From a business point of view, Word’s commenting functionality is another key selling point. With comments on Word, it’s easy to collaborate on documents or request changes without having to create a new version of the document every time.
4. Ideal for dispersed teams
Word isn’t the only collaborative element you’ll find on Microsoft 365. With so many people working remotely for the foreseeable future, collaborative communication platforms are becoming ever more popular, and necessary.
Microsoft Teams is a major player in the market and comes with the Microsoft 365 Business package. Using Teams, users can host conference phone and video calls and collaborate on files in real time. The software also pools your company’s Microsoft apps in one place, so you can work on complex tasks collaboratively. Read our Microsoft Teams review to find out more.
5. Excellent email facilities

Microsoft Outlook is one of the best-known email clients, and comes as standard with Microsoft 365, where it can also be paired with Microsoft Exchange, a business-focused email server that provides secure email delivery, prioritised mail facilities, and automated and synced calendars. Other email perks include a 50GB mailbox, cloud-based management, a custom domain name, and more.
6. Top-notch cyber security
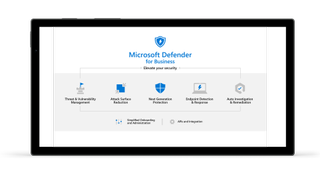
Microsoft ensures a very high level of security protection for its products, primarily through Microsoft Defender. Emails are protected with defences against multiple cybersecurity threats, including malware, viruses, ransomware, phishing, and general spam.
It’s also possible to integrate password protection on files and other business information, and you can even prompt users within your network to update their security credentials on a regular basis. Additionally, you can restrict the copying or saving of business-specific information to third-party apps, and remotely wipe compromised files or databases.
7. Financial management and planning is simplified
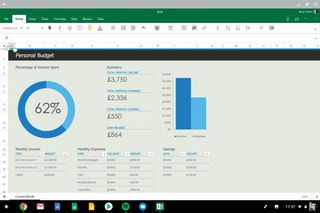
Microsoft Excel is a well-known tool for creating and managing spreadsheets, which can be used by your HR and finance teams to monitor the incoming and outgoing assets for your company. The latest version of Excel also includes advanced reporting and data visualisation features, so you can present these stats easily.
Another app, Microsoft Planner, enables you to manage your company tasks with ease. A very user-friendly application, Planner also includes data visualisation tools that any member of your team can use, regardless of their IT literacy.
8. Mobile and web accessibility
A standout feature of the whole Microsoft 365 platform is its accessibility. There are web and mobile versions of all the core apps. This means users can work on any company-related tasks they may need to without the requirement of being present in the office. Each user can connect up to five iOS or Android mobile devices.
9. Build your own intranet
Collaboration between teammates on Microsoft 365 doesn’t stop at OneDrive, Word, and Teams. Microsoft SharePoint takes this one step further. Using SharePoint, users can actually create intranet sites to share and showcase work internally.
At its core, SharePoint is a platform for creating specific team and project sites that employees can visit, and collaborate on by sharing news, files, and other media. On a company-wide level, SharePoint can be used to create an intranet system to engage with teams both inside and outside of the office environment.
10. Presentation tools
You might remember Microsoft PowerPoint from school or college. But this presentation software has come a long way since the WordArt days. Now, it can be used to create professional business presentations that can be shared easily, and include interactive elements too.
The latest version of PowerPoint includes speech-to-text features, 3D animations, and even an AI-powered presenter coach that enables you to nail down your presentation techniques.
Summary
Microsoft 365 is the platform to beat. As a tool for business, it provides everything you need to plan future strategies, manage your business assets, communicate with your team and customers, and present new ideas.
Some of the apps included, such as Microsoft Teams and Microsoft Word, are market-leading services all on their own - coupled together, they create a software package that’s hard to beat.
Kieron is a freelance science and technology journalist with more than a decade of experience writing for magazines in print and online. Today, his focus is on cybersecurity, blockchain, and emerging tech.





