How to turn on Windows Defender
A simple guide on how to turn on Windows Defender in Windows 10 and Windows 11, and turn it off again if necessary
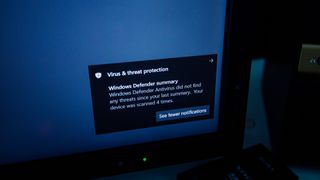
Windows Defender has provided PCs with base-level protection for a number of years now, and its capabilities improve with every iteration. In order to help you access the tool, we've put together a simple guide on how to turn on Windows Defender in Windows 10 and Windows 11.
Windows Defender has appeared on every version of Windows since Vista and can still be found on the presently supported versions, Windows 10 and Windows 11, although it has expanded to cover a variety of security tools since its initial launch.
Given it is proprietary software, Microsoft will regularly inform you if Windows Defender is turned on or off, and will direct you to the screen where you can turn it on if you so wish. If that hasn't happened, you can turn it on manually.
Defender is technically the anti-malware component of Windows, but these days it also controls a bunch of other security tools as part of the OS. Unfortunately, accessing the correct interface can be challenge depending on what version of Windows you're running, and what update you're on, as the user interface has updated a number of times.
How to turn on and manage Windows Defender
How to check if Windows Defender is running
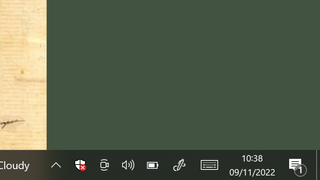
The first thing you'll want to do is check whether Windows Defender is on or off.
- To do this, take a look at the notifications area along the Taskbar (to the left of the time display, and just before the end of the Taskbar).
- Look for a small icon resembling a shield - this may be found in items that have been hidden from view. Clicking the upwards-pointing arrow should expand the icon tray and show all apps running.
The Windows Defender icon should appear in this tray with a red cross (X) if some part of the security suite has been turned off, or a yellow exclamation mark if there is some issue with your device's security. If there are no crosses or exclamation marks, your Windows security is on and is running as normal.
How to turn on Windows Defender in Windows 10 and Windows 11
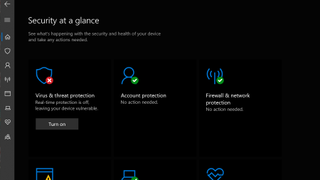
If you see that Windows Defender is turned off, you can do the following to switch it on:
- Click the Start menu
- Type "windows security" into the search bar
- Click the Windows Security app
- Click 'Turn on' under 'Virus and threat protection'
If 'Turn on' has not appeared on screen:
- Click the 'Virus and threat protection' tool listed under 'Security at a glance'
- Scroll down to 'Virus & threat protection settings'
- Click 'manage settings'
- Click the toggle button for each function to turn them on
Note: You can also access every other Windows Security Center function using this method - simply click 'Turn on' displayed under each tool to enable them.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.
Following recent updates, the above process is the same across Windows 10 and Windows 11, however on certain older versions of Windows 10 you may find that the old UI presents itself. It's worth upgrading to the latest version of your operating system to avoid having to deal with these legacy interfaces.
How to turn off Windows Defender

Generally speaking, Windows Defender will automatically protect your system unless you either manually disable it or install a different security suite. In the event you want to disable Windows Defender, you can do the following:
- Click the Start Menu icon and search "Windows Security"
- From here, select 'Virus & threat protection'
- Scroll down to 'Virus & threat protection settings'
- Click 'manage settings'
- Click the toggle buttons on each function to turn them off
- You will then be notified with a pop up that the program is off
Why you should use Windows Defender
With each passing year, Windows Defender - which comes free with every copy of Windows - has grown more effective at stopping security threats to the point where its performance beats that of some other third-party paid solutions. It was once the case where it was recommended that businesses running Windows machines should invest in an aftermarket antivirus or antimalware product installed to maintain protection from malware and other nefarious tools used by hackers.
How to build your resilience against application layer threats
Addressing security threats with a consolidated cloud-based platform approach
With the performance difference between Windows Defender and other security products being so negligible, nowadays it’s generally safe to rely on it for basic security protection. For small businesses without an expansive IT estate, Microsoft Defender for Business - the SMB-focused paid-for equivalent, offers a more comprehensive yet affordable alternative to the basic consumer-grade protection of Windows Defender. It costs just £2.30 per user per month and claims to protect against the most common security threats that SMBs face.
Those that want to take cyber security seriously would need to invest in a little more than a small fee for Windows Defender’s business-oriented cousin, though. And organisations with larger tech stacks will also want to shell out for a more robust suite of enterprise-grade cyber security products such as endpoint protection, identity and access management solutions, extended detection and response (XDR), email security, and more.
Regardless, Windows Defender is now a seriously admirable starting point for most users. The protections it offers, such as 100% accuracy in malware detections - including zero-day exploits, are impressive given that it’s entirely free to owners of PCs running Windows 10 and Windows 11.

Connor Jones has been at the forefront of global cyber security news coverage for the past few years, breaking developments on major stories such as LockBit’s ransomware attack on Royal Mail International, and many others. He has also made sporadic appearances on the ITPro Podcast discussing topics from home desk setups all the way to hacking systems using prosthetic limbs. He has a master’s degree in Magazine Journalism from the University of Sheffield, and has previously written for the likes of Red Bull Esports and UNILAD tech during his career that started in 2015.




