The best presentation software for 2024
Investing in the best presentation software helps bring your slide ideas to life easily and impactfully

Delivering a presentation in the workplace can be a stressful experience, but the best presentation software can help you get your message across more confidently. With the backing of a convincing deck filled with powerful imagery and data, anyone can deliver a top-notch presentation.
Luckily for business users, there’s no shortage of choice when it comes to tools that can help you create the best presentations possible. We’ve brought together the best presentation software in the five best offerings from Microsoft, Visme, Google, Prezi, and Slidebean.
Whether you plan to present remotely via a video conferencing system or in-person, pay $180 per year, or nothing at all – you’re likely to find the perfect software for your presentation in one of the five options detailed below. Once you’ve decided which one suits you best, you’ll just have to work on your public speaking skills.
1. Microsoft PowerPoint
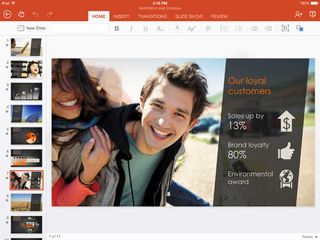
Supported operating systems: Windows, macOS, iOS, and Android
Free tier: Yes
Ever since it was first released in 1987, PowerPoint has been one of the top contenders for the title of best presentation software. With a powerful set of features including clean graphics and stock images, the ability to time and record slideshows, and even have generative AI produce text, images, or entire slides if you pay for Copilot for Microsoft 365.
Other PowerPoint features include support for 3D objects, limited image editing, and the ability to produce detailed infographics.
As part of the Microsoft Office 365 software suite, PowerPoint is widely used in conjunction with Excel, Outlook, Word, and Access. The online version of PowerPoint allows users to collaborate on a slideshow in real-time.
Microsoft 365 business subscriptions start at $6 (or £4.90) per user per month, depending on options and add-ons. If you’re not interested in the other apps in the suite, you can also purchase PowerPoint as a standalone app for a one-time fee of $159.99 (or £149.99).
2. Google Slides
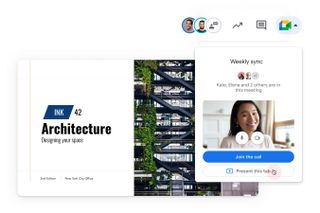
Supported operating systems: Windows, macOS, iOS, ChromeOS, and Android
Free tier: Yes
Google Slides was built with collaboration at its heart and operates very similarly to Microsoft PowerPoint. As part of the Google Workspace (formerly G Suite) set of applications, Google Slides is available for free with any Google account and works seamlessly with Google Drive and Google Sheets.
You can import PPSX files from Microsoft PowerPoint directly into Google Slides and also download slides in a range of formats when finished. This allows for a good degree of flexibility and inter-compatibility when using Google Slides, perfect for businesses that rely on a mixture of Google Workspace and Office 365 or those whose customers are entirely reliant on a platform outside of Google.
Suited for the hybrid working era, users can deliver presentations on Google Meet video calls directly from Slides. A built-in Q&A feature also allows viewers to submit anonymous questions while a presenter runs through their slides.
If you choose to pay for Google Slides, you’ll be able to use more cloud storage, benefit from advanced security features, and receive more responsive tech support.
Subscriptions start at $6 (or £5) per user per month for the Business Starter plan. For more cloud storage, video meeting options, and recording there’s also the Business Standard plan at $12 (or £10) per user per month and the Business Plus plan for $18 (or £15) per user per month.
Topping the offerings is a customizable Enterprise offering, with quotes available on a per-business basis via the Google Workspace sales team. Those looking to leverage features similar to Microsoft’s Copilot in PowerPoint will be glad to know there’s also the option of using Google Gemini in Google Workspace starting at $20 per month.
3. Prezi
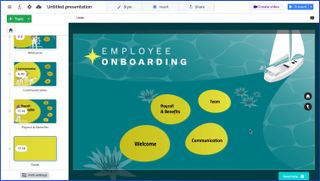
Supported operating systems: Windows, macOS, iOS, and Android
Free tier: Yes
As presentation software goes, Prezi might be the best for pure focus on images. Users can zoom into slides to a greater degree than in competing software and are encouraged to turn the canvas at different angles while presenting or insert seamless transitions to keep your audience engaged.
Additionally, Prezi makes it easy to import and embed a PDF file into your presentation. You may also choose to incorporate live or recorded videos into your presentations via video in video. Convenient and secure, Prezi’s “Go Live” feature lets you share your recordings with popular video conferencing tools, including Zoom, Webex, and others.
Prezi also has its own integrated AI assistant, which suggests templates based on text input and can reword text to improve its readability. The Basic plan is free and lets you create and share up to five projects but Prezi also offers flexible business tiers: Plus, Premium, and Teams.
‘Plus’ plans cost $15 (or £15) per month and enable users to create unlimited projects, infographics, import slides from Microsoft PowerPoint, export decks as PDFs, and create voice-overs for presentations. At the ‘Premium’ level, which costs $19 (or £19) per month, users get presentation analytics, advanced online training, as well as phone and chat support.
Topping the price list is the Teams plan, which starts at $19 (or £19) per month and includes admin controls, custom branding, integration with Slack, and secure single sign-on (SSO) among other benefits. Keep in mind, Prezi bills those monthly fees annually, but you can take advantage of a 14-day free trial.
4. Visme

Supported operating systems: Windows, Linux, macOS, iOS, and Android
Free tier: Yes
With Visme, you can run your presentation online or offline, collaborate with teams, connect charts to live data, and more. Visme’s intuitive drag-and-drop interface provides granular content control, making customization quick and easy. You can also add animated assets, forms, and surveys to a Visme presentation.
What’s more, Visme’s analytics feature lets you track traffic on public Visme projects. When someone views a public Visme project, the software detects and compiles the source address, number of unique visitors, and each visit’s duration. Visme then visualizes the metrics into an easy-to-understand analytical graph, accessible through the dashboard. You can also download the metrics as Excel reports.
Visme offers a free plan that allows up to five projects and includes limited templates, charts and widgets, 100 MB of storage, the ability to download JPG files, and more.

Three-step guide to modern customer experience
Support the critical role CX plays in your business
Paid Visme plans come in three variants: Starter ($29 per month or $147 per year), Pro ($59 per month or $297 per year), and Visme for Teams (contact sales for pricing).
The Starter plan adds onto the free plan with up to 250 MB of storage, premium assets and templates, no Visme branding, PDF download, 24/7 phone and chat support, and more. The Business plan offers 3 GB of storage, multiple file download types, a branding kit, privacy controls, and more.
For large corporations, the Enterprise plan has custom pricing. This builds upon the Business plan with 25 GB of storage, single-sign-on ability, two-factor authentication, a custom subdomain, deep analytics, training and onboarding, and more.
5. Slidebean
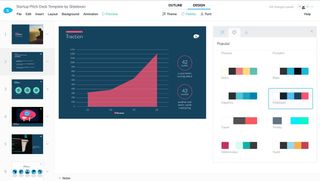
Supported operating systems: Windows, macOS, iOS, and Android
Free tier: Yes
Standing out from the conventional, Slidebean is an AI-powered, web-based multimedia presentation tool. It can design and format your slides automatically as you type. Furthermore, this tool lets you combine a wide range of media, including videos, PDF files, web pages, and Prezi and PowerPoint presentations, to name a few.
From sales decks to business proposals, Slidebean’s ready-to-use templates offer smart content suggestions to keep presentations informative yet creative. You may even choose to remotely control your SlideDog presentations from a desktop or your smartphone.
Slidebean’s free plan includes unlimited access to its AI-powered editor, pre-built templates, and media galleries. Its paid plan, All-Access, allows users to share and export presentations to PDF and PPT, track views and activity on slides, browse over 30,000 investor contacts, and access over $15,000 in discounts on startup tools.
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.




